Archive
Join the MVP’s to discover what’s new in Windows Server 2019 and System Center 2019
As Microsoft release Windows Server 2019 and System Center 2019, you may want to get a grasp on the staggering amount of new features, improvements and updates included and hear from the Microsoft MVP’s and Windows Insiders.

On October 3rd, Microsoft MVPs Andy Syrewicze and Rob Corradini, alongside former Microsoft Senior Technical Evangelist Symon Perriman will be running an expert panel hosted by Altaro were you can get a full grasp of the both Windows Server and System Center 2019 and a closer look at some standout features that will have the biggest impact to organizations looking to upgrade to Window Server 2019.
What to expect from the webinar?
- Next-generation management with Windows Admin Center
- Windows Server 2019 Hyper-V enhancements and Failover Clustering
- Windows and Hyper-V Containers on the Windows platform
- Easy migrations using Storage Migration Service
- And much more!
Got any questions about Windows Server 2019? Of course you do. Get answers direct from the experts during the webinar Q&A!
With the knowledge gained in this webinar, you’ll be ready to take full advantage of the new possibilities Windows Server 2019 brings to the table, and in doing so, keep your organization ready for the next generation of IT workloads.
Shielded VM’s: Virtualization security is a major investment area in Hyper-V 2016
 SECURITY – Protecting the company data should be a priority.
SECURITY – Protecting the company data should be a priority.
Protecting a Virtual Machine(VM) guest from a possible host compromised as well as the certain that on a 3rd party hosting environment your VM will be protected in addition to the protection applied to the hosts is a major investment area in Hyper-V 2016.
If you find that Microsoft is helping you and your business and find it has amazing technologies as I as do, please help me out by recommending it on Recomazing a new tech platform where socially connected networks store and share trusted recommendations. Please click here to help our community.
Taking into consideration that a VM is a file, stored somewhere on a storage on locally in the Hyper-v host, it needs to be protected from attacks to the storage system, the network, while it is backed up or taken or copied to other systems.
To help protect against compromised fabric, Windows Server 2016 Hyper-V introduces Shielded VMs. A Shielded VM, requires a VM to be created as generation 2, which has a virtual TPM, is encrypted using BitLocker and can only run on healthy and approved hosts in the fabric. So, if someone copy either maliciously or accidentally the VM to a non-approved host, the VM (which is encrypted), won’t start and cannot be used to be mounted to allow access to it’s file system.
Shielded VM’s use several features to make it harder for Host administrators and malware on the host to inspect, tamper with, or steal data from the state of a shielded virtual machine. Data and state is encrypted, Hyper-V administrators can’t see the video output and disks, and the virtual machines can be restricted to run only on known, healthy hosts, as determined by a Host Guardian Server.
A configured Shielded VM has:
- BitLocker encrypted disks
- A hardened VM worker process (VMWP) that helps prevent inspection and tampering
- Automatically encrypted live migration traffic as well as encryption of its runtime state file, saved state, checkpoints and even Hyper-V Replica files (from 2016 TP5)
- Blocked console access
- Blocked PowerShell Direct
- Blocked Guest File Copy Integration Components
- Blocked services that provide possible paths from a user or process with administrative privileges to the VM.

Image Source: Microsoft – https://technet.microsoft.com/en-us/library/mt599611.aspx
With the release of Windows Server 2016 TP5, the Hyper-V team at Microsoft made shielded virtual machines compatible with Hyper-V Replica. As with copying/moving the VM, to replicate a shielded VM, the host you want to replicate to must be authorized to run that shielded VM.
The Host Guardian Service supports two different deployments of a Guarded fabric (attestation modes): TPM-trusted attestation (Hardware based) and Admin-trusted attestation (AD based).
I hope you walk away with a better understanding of the Hyper-V Shielded VM solution from this post.
Hyper-V. CSV Volumes pause states 5120: Workaround
Microsoft is aware that after installing KB3126593 (MS16-014) there may be an issue that causes loss of network packets.
This may cause Cluster Shared Volumes (CSV) on the nodes Failover Clusters to going into a paused state with an event ID 5120 in the System event log what indicates “Status c000020c – STATUS_CONNECTION_DISCONNECTED”.
You will also find that, on the node that owns the CSV volume(s), there will be an event 7031 with the source: “Service Control Manager”, which indicates “The Windows Firewall Service terminated unexpectedly”.
Troubleshooting Cluster Shared Volume Auto-Pauses – Event 5120. https://blogs.msdn.microsoft.com/clustering/2014/12/08/troubleshooting-cluster-shared-volume-auto-pauses-event-5120/
Microsoft is aware of this problem and are working on a fix. But until it is release here is what you could do to get around this issue:
Option 1: Disable the Firewall LOGGING for all profiles (domain, private, public). (just the logging, not the firewall . You don’t want to be un-protected)
1. Start the Windows Firewall with Advanced Security management console (wf.msc)
2. Right-click Windows Firewall with Advanced Security on Local Computer and select Properties
3. For all profiles (Domain, Private, Public), under Logging, click Customize. Set Log Dropped Packets and Log Successful connections to NO.
Option 2. Uninstall https://support.microsoft.com/en-us/kb/3126593 from the systems.
I will post an update once Microsoft releases the Hotfix.
Supercharging performance of your Hyper-V
If you are an expert in Hyper-V or just started playing with it, I recommend you download the Hyper-V ebook provided by Altaro.
The ebook is divided in 2 sections: (1) Diagnosing and Remediating Performance Issues and (2) Planning is Better than Remediation.
It will help you better plan your next Hyper-V deployment and how could you make the most of your existing deployment, through practical hands-on tips as well as background information you will learn how Hyper-V (and virtualization in general) affects performance and how to find issues in storage, CPU, memory and network components. This is followed by a look at planning hosts, VMs, storage, networking and management for maximum performance.
What the book covers:
- Diagnosing and remediating Storage, CPU, Memory, and Network performance issues
- Using Windows Performance Monitor and PAL to facilitate system and VM monitoring
- Manage planning of Hosts, VMs, Storage, Networking, to minimize the risk of performance issues
Azure ASR’s SLA-backed enhanced VMware to Azure solution is now ready to replicate your on-premises workloads to Azure
You heard right. Microsoft has launched an enhanced version of its Azure Site Recovery (ASR) targeted especially for VMware customers.
The concept of ASR is very simple: organisations will be able to replicate their VMware virtual machines (VMs) to Azure, update and then run them in Azure as a disaster recovery option. They will be charged a small amount by VM but won’t have to pay for compute or storage until the VM is up and running in Azure.
To note, Azure Site Recovery, as part of Microsoft Operations Management Suite (OMS), enables your organisation to gain control and manage your workloads no matter the source: Azure, AWS, Windows Server, Linux, VMware or OpenStack.
Some of the key ASR characteristics:
- With non-disruptive recovery testing, you can easily test the failover of your VMware virtual machines to Azure within minutes, and validate your workload’s performance in Azure, without impacting on-going replication or the production workload.
- With ASR-integrated failback, start replicating your Azure virtual machines back to your on-premises ESXi environment, and failback to the original or an alternate location when your on-premises site is once again available for use.
- Heterogeneous workload support, automated VMware vCenter Server discovery
- Continuous data protection (CDP), one-click failovers with ASR Recovery Plan
- Rich health monitoring and e-mail notifications.
I’ve been working with ASR for a while and I definitely recommend it.

Source:https://azure.microsoft.com/en-us/documentation/articles/site-recovery-vmware-to-azure-classic/
Ready to start using ASR? Check out additional product information, to start replicating your workloads to Microsoft Azure using Azure Site Recovery today. You can use the powerful replication capabilities of Site Recovery for 31 days at no charge for every new physical server or virtual machine that you replicate.
You can read the announcement at https://azure.microsoft.com/en-us/blog/ga-enhanced-migration-and-disaster-recovery-for-vmware-virtual-machines-and-physical-servers-to-azure-using-asr/
Technologies that work together to create Microsoft’s SDN solutions
With the upcoming Windows 2016 and System Center 2016, there will be many technologies that will work together to create Microsoft’s Software Defined Networking (SDN) solutions and the best part is that you can already check them by downloading and deploying Windows 2016 and System Center 2016 Technical Preview.
- Hyper-V Network Virtualization, which enables virtualization of tenant networks on top of a shared physical network infrastructure. , which are being performed by hardware appliances (such as load balancers, firewalls, routers, switches, and so on) are increasingly being virtualized as virtual appliances. Microsoft has virtualized networks, switches, gateways, NATs, load balancers, and firewalls.
- Network Controller, which provides a centralized, programmable point of automation to manage, configure, monitor, and troubleshoot virtual and physical network infrastructure in your datacenter.
- RAS Gateway for High Availability and failover, which can be deployed in multitenant mode to provide network traffic routing to and from virtual and physical networks, including the Internet.
- Software Load Balancing (SLB) for SDN, which can be used to evenly distribute tenant and tenant sub-networks traffic among virtual network resources. The Windows Server SLB enables multiple servers to host the same workload, providing high availability and scalability.
- Datacenter Firewall. A new service. It is a network layer, 5-tuple (protocol, source and destination port numbers, source and destination IP addresses), stateful, multitenant firewall. When deployed and offered as a service by the service provider, tenant administrators can install and configure firewall policies to help protect their virtual networks from unwanted traffic originating from Internet and intranet networks.
- Remote Direct Memory Access (RDMA) and Switch Embedded Teaming (SET). When you use a converged NIC to combine both RDMA and Ethernet traffic using a single network adapter, it will help you reduce the capital expenditures that are associated with each server in your datacenter, because you need fewer network adapters to manage different types of traffic per server. The converged NIC allows you to use a single network adapter for management, Remote Direct Memory Access (RDMA)-enabled storage, and tenant traffic. SET is a NIC Teaming solution that is integrated in the Hyper-V Virtual Switch. SET allows the teaming of up to eight physical NICS into a single SET team, which improves availability and provides failover.
- Border Gateway Protocol (BGP). When configured Border Gateway Protocol (BGP) provides you with the ability to manage the routing of network traffic between your tenants’ VM networks and their remote sites. BGP reduces the need for manual route configuration on routers because it is a dynamic routing protocol, and automatically learns routes between sites that are connected by using site-to-site VPN connections.
- System Center. VMM can be used to deploy Software Defined Networks
Source: https://technet.microsoft.com/en-us/library/mt590952.aspx
Microsoft Windows Server 2016 TP4 released
Microsoft today announced the release of Windows Server 2016 and System Center 2016 Technical Preview 4.

This new build includes new features that enables hybrid datacenter solutions.
The three main features: Hyper-V Containers, Software-defined datacenter capabilities and increase agility and Enhanced management capabilities:
Hyper-V: Now includes an early preview of nested virtualization, along with Direct Device Assignment, and improved PowerShell support for VM upgrades. Nested virtualization can be used in dev and test scenarios and is a key enabling technology for Hyper-V Containers.
- Networking: high availability for the network controller, better East-West load balancing, enhanced container networking, and support for live migration. New: Virtual Machine Multi-Queue to enable 10G+ performance.
- Storage: Storage Spaces Direct to support all-flash configurations with NVMe SSD and SATA SSD devices, and Erasure Coding for increased storage efficiency. Also in this release, support for Storage Health Service provides easier health monitoring and more streamlined operations, with a single monitoring point per cluster. Storage QoS now supports adjusting the normalization size of the algorithm from the current default 8 KB settings. Additional enhancements are designed for increased control, such as maximum bandwidth settings for a VHD/X.
- Security: Enhancements to shielded VMs and the Host Guardian Service are directed toward ensuring readiness for production environments. Just Enough Administration, which limits administrator rights for additional security, has been expanded to domain controllers and server maintenance roles.
Make innovation easier with Windows Server 2016 and System Center 2016 Technical Preview 4.
Core enhancements in System Center 2016 Technical Preview 4 include:
- Advanced software-defined datacenter support for Windows Server 2016 including new technologies such as patching of hosts while provisioning, simplified logical network creation, scale-out file server with Storage Spaces Direct and SAN storage automation, and improved storage monitoring.
- Protecting customer IP through shielded VM’s and Guardian Host deployment and management
- Easy to use monitoring improvements in Operations Manager through data-driven management of alerts and enhanced visualization
Download Windows Server 2016 Technical Preview 4: https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-technical-preview
Download System Center 2016 Technical Preview 4: https://www.microsoft.com/en-us/evalcenter/evaluate-system-center-technical-preview
Hybrid Cloud Computing with Microsoft and Red Hat
Microsoft and Red Hat announced a partnership that will help customers embrace hybrid cloud computing by providing greater choice and flexibility deploying Red Hat solutions on Microsoft Azure.
 Red Hat Enterprise Linux will be the preferred option for enterprise Linux workloads on Microsoft Azure.
Red Hat Enterprise Linux will be the preferred option for enterprise Linux workloads on Microsoft Azure.
Microsoft Azure will become a Red Hat Certified Cloud and Service Provider, enabling customers to run their Red Hat Enterprise Linux applications and workloads on Microsoft Azure. Red Hat Cloud Access subscribers will be able to bring their own virtual machine images to run in Microsoft Azure.
Customers will be offered cross-platform, cross-company support spanning the Microsoft and Red Hat offerings in an integrated way, unlike any previous partnership in the public cloud. By co-locating support teams on the same premises, the experience will be simple and seamless, at cloud speed.
Red Hat CloudForms will interoperate with Microsoft Azure and Microsoft System Center Virtual Machine Manager, offering Red Hat CloudForms customers the ability to manage Red Hat Enterprise Linux on both Hyper-V and Microsoft Azure. Support for managing Azure workloads from Red Hat CloudForms is expected to be added in the next few months, extending the existing System Center capabilities for managing Red Hat Enterprise Linux
In addition, Expanding on the preview of .NET on Linux announced by Microsoft in April, developers will have access to .NET technologies across Red Hat offerings, including Red Hat OpenShift and Red Hat Enterprise Linux, jointly backed by Microsoft and Red Hat. Red Hat Enterprise Linux will be the primary development and reference operating system for .NET Core on Linux.
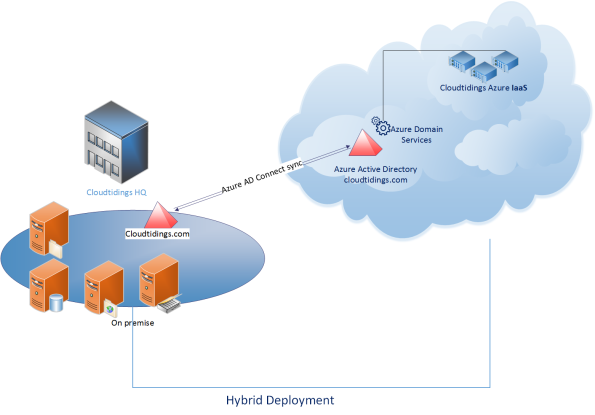
Cloud domain controller as a services with @Azure AD Domain Services @microsoftenterprise
That’s right Cloud AD as a services. A fully managed domain by Microsoft : Azure AD Domain Services to manage Azure IaaS workloads.
Azure AD Domain Services It’s a cloud based service which gives you a fully Windows Server Active Directory compatible set of API’s and protocols, delivered as a managed Azure service.
You don’t need to provision a Virtual Machine running Domain Controller on Azure as a IaaS anymore and have those domain controllers synchronize to their on-premises Active Directory servers using a VPN/Expressroute connection.
You can now turn on support for all the critical directory capabilities your application and server VM’s need, including Kerberos, NTLM, GROUP POLICY and LDAP.
For scenarios like Disaster Recovery and hybrid cloud deployments, it is just perfect. It means a full value of Windows Server AD in the cloud domain, without having to deploy, manage, monitor and patch domain controllers.
There are many scenarios that can be explored with this new feature.
You can enable Azure AD Domain Services for any existing Azure AD tenant – the same tenant you use with Office 365 or other SaaS applications. Azure AD Domain Services are available now.
For pricing, please check : http://azure.microsoft.com/pricing/details/active-directory-ds/
To start:
- You already deployed Azure AD Connect (to sync identity information from the on-premises Active Directory to your Azure AD tenant. This includes user accounts, their credential hashes for authentication (password sync) and group memberships)
- Create the ‘AAD DC Administrators’ group and then add all users who need to be administrators on the managed domain to it. These administrators will be able to join machines to the domain and to configure group policy for the domain.
- Configure the Network. Select or create the Azure virtual network you’d like to make domain services available in. Ensure the following:
- The virtual network belongs to a region supported by Azure AD Domain Services. See the region page for details.
- Ensure the virtual network is a regional virtual network and doesn’t use the legacy affinity groups mechanism.
- Ensure your workloads deployed in Azure Infrastructure services are connected to this virtual network

- Enable Azure AD Domain Services for your Azure AD tenant, by going to the Configure tab of your Directory, selecting Yes on ‘Enable Domain Services for This Domain’, specifying the domain name and selecting the Azure Virtual Network. Click on Save to confirm.
- Update DNS settings for the Azure virtual network to point to the new IP address of the Azure AD Domain Services you just enabled.
- Enable synchronization of legacy credential hashes to Azure AD Domain Services. This is a required step. By default, Azure AD does not store the credential hashes required for NTLM/Kerberos authentication. You need to populate these credential hashes in Azure AD so users can use them to authenticate against the domain.
A few salient aspects of the managed domain that is provisioned by Azure AD Domain Services are as follows:
- This is a stand-alone managed domain. It is NOT an extension of your on-premises domain.
- You won’t need to manage, patch or monitor this this managed domain.
- There is no need to manage AD replication to this domain. User accounts, group memberships and credentials from your on-premises directory are already synchronized to Azure AD via Azure AD Connect.
- Since the domain is managed by Azure AD Domain Services, there is no Domain Administrator or Enterprise Administrator privileges on this domain.
Challenges of Cloud Adoption
The Cloud approach addresses elastic scale, agility, costs and time to market, by allowing organizations not only to deploy a solution quickly but also to scale up/down based on demand. Cloud adoption is sky rocketing, there’s no doubt about it. However, when it comes to investments in the Cloud, how are you planning and assessing business and IT requirements?
- Is your current IT infrastructure and resources meeting the required business SLA’s?
- How you foreseeing capacity issues?
- Are you connecting IT resources to business outcomes and unifying IT processes with business cycles?
- How does your business maintain the system availability and resilience?
- How are you maximizing the utilization of the resources within your IT infrastructure?
With this whitepaper, we will help you find the answer to those questions, covering the challenges in deployment, management and automation phases with some tips and considerations.
Download the whitepaper
You can also register for Savision’s complimentary webinar, presented by MVP Alessandro Cardoso on Adopting the Cloud. The webinar will be presented by MVP Alessandro Cardoso, and will be co-hosted by Savision’s co-founder and VP of Product Management, Dennis Rietvink.
Register for the webinar: