Archive
Becoming a Azure Sentinel expert
I have been working on Azure Sentinel projects for the past 12 months and writing IP which uses Azure Sentinel, a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.

Recently, while working on a Sentinel project for a major enterprise I became aware of a training that Ofer Shezaf from Microsoft has shared and I highly recommend for those who would like to learn and become an expert on Azure Sentinel to check out the the material and curriculum.
The training program includes 16 modules and includes presentations, relevant product documentation, blog posts, and other resources and if you are already familiar with Sentinel, check out the module 9, my preferred one.
Overview
– Module 1: Technical overview
– Module 2: Azure Sentinel role
Designing Your Deployment
– Module 3: Cloud architecture and multi-workspace/tenant support
– Module 4: Collecting events
– Module 5: Log Management
– Module 6: Integrating threat intelligence
Creating Content
– Module 7: Kusto Query Language (KQL) – the starting point
– Module 8: Writing rules to implement detection
– Module 9: Creating playbooks to implement SOAR
– Module 10: Creating workbooks to implement dashboards and apps
– Module 11: Implementing use cases
Security Operations
– Module 12: A day in a SOC analyst’s life, incident management, and investigation
– Module 13: Hunting
Advanced Topics
– Module 14: Automating and integrating
– Module 15: Roadmap – since it requires an NDA, contact your Microsoft contact for details.
– Module 16: Where to go next?
You can find the training material here
Image sources: Source image: https://docs.microsoft.com/en-us/azure/sentinel/overview
Our new SIEM tool: Microsoft Azure Sentinel, intelligent security analytics for your entire enterprise
As we know, many legitimate threats go unnoticed and with the unsurprising high volume of alerts and your team spending far too much time in infrastructure setup or BAU tasks, you need a solution that empowers your existing SecOps team to see the threats clearer and eliminate the distractions.

That’s why we reimagined the SIEM tool as a new cloud-native solution called Microsoft Azure Sentinel. Azure Sentinel provides intelligent security analytics at cloud scale for your entire enterprise. Azure Sentinel makes it easy to collect security data across your entire hybrid organization from devices, to users, to apps, to servers on any cloud.
Collect data across your enterprise easily – With Azure Sentinel you can aggregate all security data with built-in connectors, native integration of Microsoft signals, and support for industry standard log formats like common event format and syslog.
Analyze and detect threats quickly with AI on your side – Security analysts face a huge burden from triaging as they sift through a sea of alerts, and correlate alerts from different products manually or using a traditional correlation engine.
Investigate and hunt for suspicious activities – Graphical and AI-based investigation will reduce the time it takes to understand the full scope of an attack and its impact. You can visualize the attack and take quick actions in the same dashboard.
Automate common tasks and threat response – While AI sharpens your focus on finding problems, once you have solved the problem you don’t want to keep finding the same problems over and over – rather you want to automate response to these issues.
More Information:
https://azure.microsoft.com/en-us/services/azure-sentinel/#documentation
Azure Sentinel preview is free
There will be no charges specific to Azure Sentinel during the preview. Pricing for Azure Sentinel will be announced in the future and a notice will be provided prior to the end of the preview. Should you choose to continue using Azure Sentinel after the notice period, you will be billed at the applicable rates
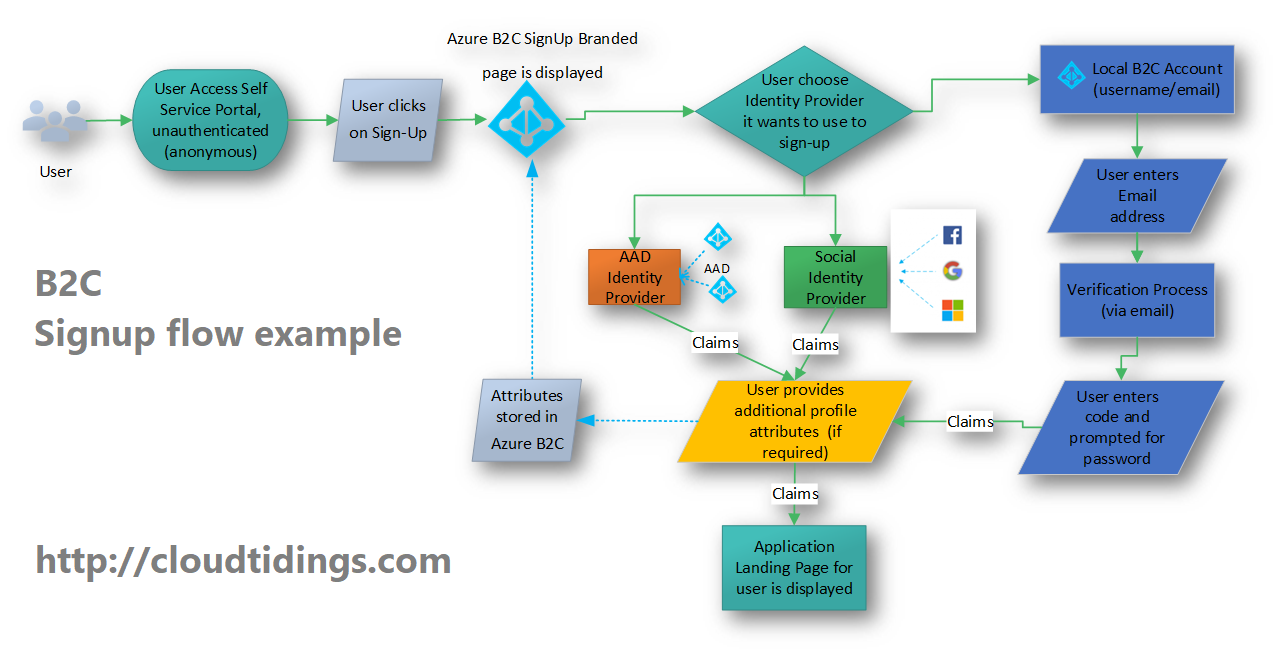
Azure B2C: Flexibility is the key
I have been working in some challenging’s Identity projects for the past 2 years and I have been amazed by the great flexibility that Azure B2C offers.
This week I am in Prague delivering an Azure Bootcamp for our
internal Microsoft team and speaking on Identity and Security and Azure B2C is one of the major points of my sessions.
In August this year I’ve completed a project that enabled a major financial institution to offer an secure and easy way for their partners/customers to sign in to access their application.
Azure Active Directory B2C is a reliable, globally-distributed service with an SLA of 99.9%, capable of supporting millions of users and billions of authentications per day, allowing users to sign in with Microsoft Accounts, Azure AD, Facebook, Google+, LinkedIn and many others, or your own Identity provider,
Customers profiles are protected through various security controls in addition to application or policy-based multi-factor authentication.
You can learn more on how to manage sign-up, sign-in, and customer profiles in your ASP.NET, desktop, or single-page Node.js applications at https://docs.microsoft.com/en-us/azure/active-directory-b2c/#step-by-step-tutorials
Join the MVP’s to discover what’s new in Windows Server 2019 and System Center 2019
As Microsoft release Windows Server 2019 and System Center 2019, you may want to get a grasp on the staggering amount of new features, improvements and updates included and hear from the Microsoft MVP’s and Windows Insiders.

On October 3rd, Microsoft MVPs Andy Syrewicze and Rob Corradini, alongside former Microsoft Senior Technical Evangelist Symon Perriman will be running an expert panel hosted by Altaro were you can get a full grasp of the both Windows Server and System Center 2019 and a closer look at some standout features that will have the biggest impact to organizations looking to upgrade to Window Server 2019.
What to expect from the webinar?
- Next-generation management with Windows Admin Center
- Windows Server 2019 Hyper-V enhancements and Failover Clustering
- Windows and Hyper-V Containers on the Windows platform
- Easy migrations using Storage Migration Service
- And much more!
Got any questions about Windows Server 2019? Of course you do. Get answers direct from the experts during the webinar Q&A!
With the knowledge gained in this webinar, you’ll be ready to take full advantage of the new possibilities Windows Server 2019 brings to the table, and in doing so, keep your organization ready for the next generation of IT workloads.
The transition to adopting cloud services is unique for every organization. What does yours look like?
- Andy Syrewicze (Microsoft MVP and Technical Evangelist – Altaro),
- Didier Van Hoye (Microsoft MVP and Infrastructure Architect – FGIA),
- Thomas Maurer (Microsoft MVP and Cloud Architect – itnetX)
There are limited seats, REGISTER NOW to save your spot
For a FREE LIVE Webinar with will focus on cloud technologies and presented as a panel-style discussion on the possibilities of cloud technologies coming out of Microsoft, including:
- Windows Server 2019 and the Software-Defined Datacenter
- New Management Experiences for Infrastructure with Windows Admin Center
- Hosting an Enterprise Grade Cloud in your datacenter with Azure Stack
- Taking your first steps into the public cloud with Azure IaaS
After watching the experts discuss the details, you’ll see that the cloud doesn’t have to be an all or nothing discussion. This webinar will prepare you for your journey by revealing the available options and how to make the most out of them!
It is a great opportunity to ask industry experts as they share their experiences working with many customers worldwide.
WHEN:
Wednesday June 13th 2018 – Presented live twice on the day
- Session 1: 2pm CEST – 5am PDT – 8am EDT
- Session 2: 6pm CEST – 9am PDT – 12pm EDT
- Twitter: https://goo.gl/f8v9mH
- Facebook: https://goo.gl/wDe7vN
- LinkedIn: https://goo.gl/go5JpL
Remove yourself as guest user of a partner organisation AD tenant

In the past, when working with partner organisations where you were invited to access shared resources or applications, in order to get your access removed/revoked you would need to contact their Global Admin and ask them to remove you. That was not an easy task!
Now, Microsoft released a Azure B2B update which will allow you to remove yourself from the partner organisation AD tenant

When a user leaves an organization, the user account is “soft deleted” in the directory.
By default, the user object moves to the Deleted users area in Azure AD but is not permanently deleted for 30 days. This soft deletion enables the administrator to restore the user account (including groups and permissions), if the user makes a request to restore the account within the 30-day period.

If you permanently delete a user, this action is irrevocable.
These highly-requested capabilities simplify and modernize your collaboration. They also empower your partner users and help you with your GDPR obligations.
You can find more information about this an other new exciting features of Azure B2B at : https://docs.microsoft.com/en-au/azure/active-directory/active-directory-b2b-leave-the-organization
If you’re interested in viewing or deleting personal data, please see the Azure Data Subject Requests for the GDPR article. If you’re looking for general info about GDPR, see the GDPR section of the Service Trust portal.
New Azure B2B Invite process.
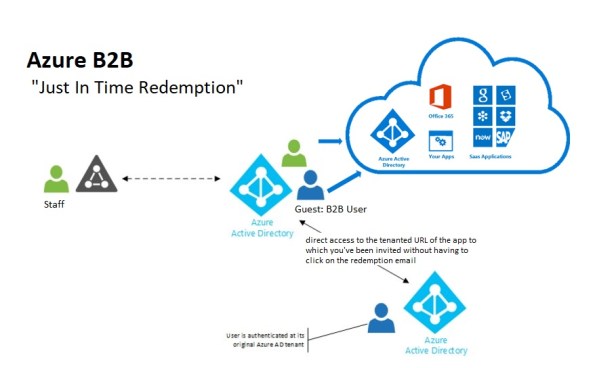 New Azure B2B Invite process: Redemption through a direct link
New Azure B2B Invite process: Redemption through a direct link
“Just in Time Redemption”.
In the past, in order for your guest/partner users to access a shared resources utilising Azure B2B Collaboration, they would have had to be invited by email to access resources/apps on your Azure Tenant. When receiving the email, your guest/partner clicks on the invitation link which will trigger its acceptance and consequent adding the guest/partner account as a guest user in your tenant and the providing access to the resources or apps you have configured.
Now, although that option still available, your guest/partner users can simply access the application you’ve invited them to. How? You can invite a guest/partner user by sending him/her a direct link to a shared app.
NEW Modernized Consent Experience. When a guest/partner user accesses your organization’s resources for the first time, they will interact with a brand new, simple, modernized consent experience.
 Image source:https://cloudblogs.microsoft.com/enterprisemobility/2018/05/14/exciting-improvements-to-the-b2b-collaboration-experience/
Image source:https://cloudblogs.microsoft.com/enterprisemobility/2018/05/14/exciting-improvements-to-the-b2b-collaboration-experience/
After any guest user signs in to access resources in a partner organization for the first time, they see a Review permissions screen.
The guest/partner user must accept the use of their information in accordance to the inviting organization’s privacy policies to continue
Upon consent, the guest/partner users will be redirected to the application shared by you.
How it works:
-
-
- You want your guest/partner user to access a specific application
- You add them as a guest user to your organization (In the Azure Portal, go to Azure Active Directory -> Users -> New Guest User)
-

- In the message invitation, type the link to the application you want them to have access to
- Now, your guest/partner user will only have to click on the link to the application to immediately access it after giving consent.
It’s very simple isn’t it?
Do you have questions on Containers? #AskBenArmstrong
Fundamentally, Containers are an isolated, resource controlled, and portable runtime environment which runs on a host machine or virtual machine and allows you to run an application or process which is packaged with all the required dependencies and configuration files on its own.
When you containerize an application, only the components needed to run this application and of course the application itself are combined into an image, which are used to create the Containers.
How are you utilising containers? Do you have questions on Containers? On Tuesday, 24th April, Microsoft Program Manager Ben Armstrong, will be answering your questions on Containers. It is a rare opportunity. Don’t miss out.
- Date and Time: Tuesday, Apr 24, 2018, 4pm CEST (7am PDT / 10am EDT) Duration: Approx. 1 hour
- Date and Time: Tuesday, Apr 24, 2018, 10am PDT / 1pm EDT (7pm CEST) Duration: Approx. 1 hour
You can also ask questions through twitter until Tuesday by including #AskBenArmstrong.
Serial Console access for both #Linux and #Windows #Azure VMs #COM1 #SerialConsole

Source: https://azure.microsoft.com/en-us/blog/virtual-machine-serial-console-access/
Now, you can debug fstab error on a Linux VM for example, with direct serial-based access and fix issues with the little effort. It’s like having a keyboard plugged into the server in Microsoft datacenter but in the comfort of your office.
Serial Console for Virtual Machines is available in all global regions! This serial connection is to COM1 serial port of the virtual machine and provides access to the virtual machine and are not related to virtual machine’s network / operating system state.
All data is sent back and forth is encrypted on the wire.All access to the serial console is currently logged in the boot diagnostics logs of the virtual machine. Access to these logs are owned and controlled by the Azure virtual machine administrator.
You can access it by going to the Azure portal and visiting the Support + Troubleshooting section.
Security Access Requirements
Serial Console access requires you to have VM Contributor or higher privileges to the virtual machine. This will ensure connection to the console is kept at the highest level of privileges to protect your system. Make sure you are using role-based access control to limit to only those administrators who should have access. All data sent back and forth is encrypted in transit.
Access to Serial console is limited to users who have VM Contributors or above access to the virtual machine. If your AAD tenant requires Multi-Factor Authentication then access to the serial console will also need MFA as its access is via Azure portal.
How to enable it:
For Linux VMs: this capability requires no changes to existing Linux VM’s and it will just start working.
For Windows VMs: it requires a few additional steps to enable it:
- Virtual machine MUST have boot diagnostics enabled
- The account using the serial console must have Contributor role for VM and the boot diagnostics storage account.
- Open the Azure portal
- In the left menu, select virtual machines.
- Click on the VM in the list. The overview page for the VM will open.
- Scroll down to the Support + Troubleshooting section and click on serial console (Preview) option. A new pane with the serial console will open and start the connection.
Note: For all platform images starting in March, Microsoft have already taken the required steps to enable the Special Administration Console (SAC) which is exposed via the Serial Console.
Windows Server 2019 now available in preview

On March 20th 2018, Microsoft announced that Windows Server 2019, which is built on the strong foundation of Windows Server 2016, are now released to Preview. You can get access to the preview build through Microsoft Insiders program.
Windows 2019 will be generally available (GA) in the second half of calendar year 2018.
Some tips:
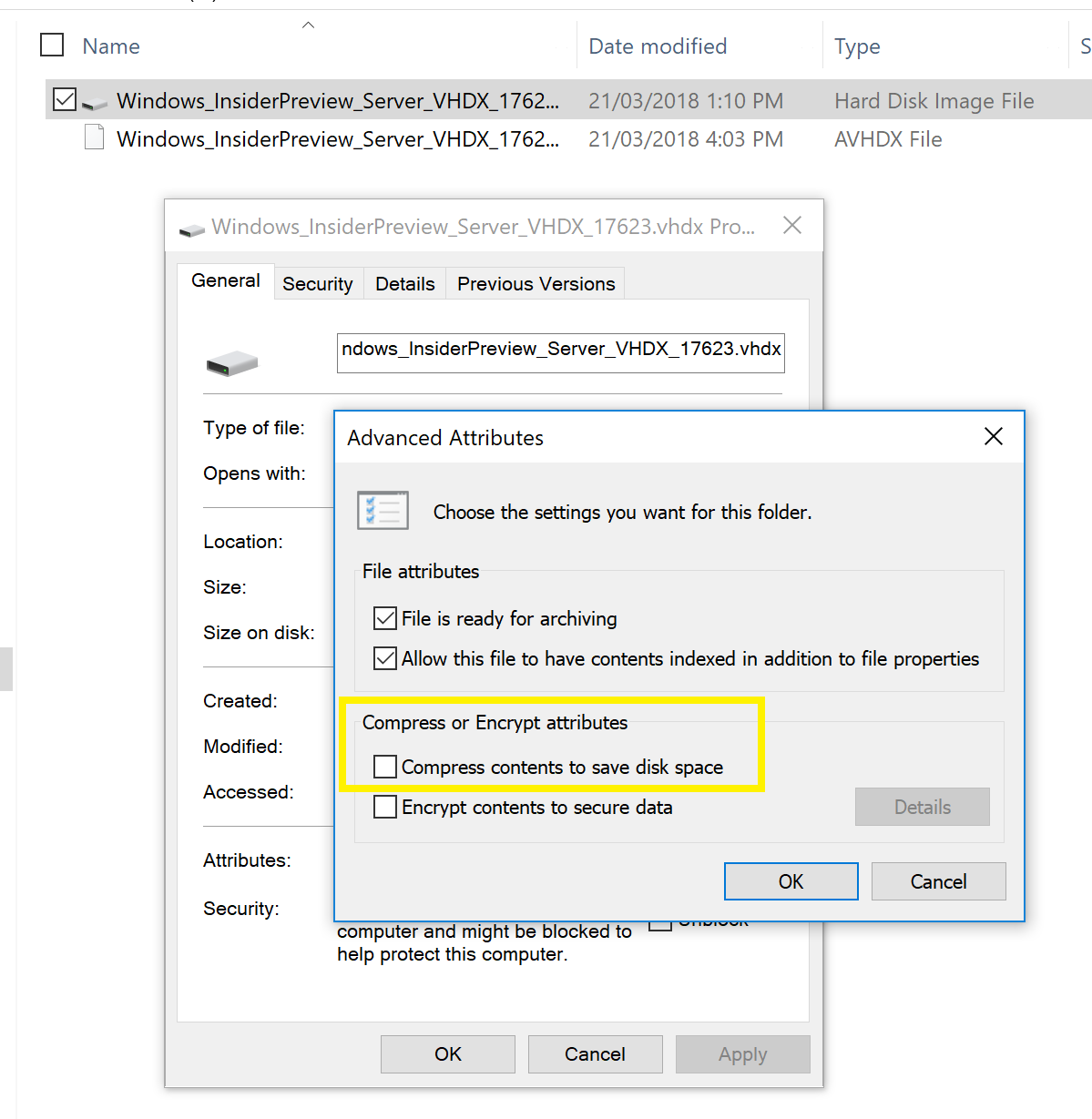
- The Windows Server vNext Semi-Annual Preview – Build 17623 is Server Core ONLY
- If you downloaded the VHDX version, as the file is compressed, make you sure you remove the compress check in the properties of the file as per below image as it will fail to start the VM if you don’t:
- Download the Windows Server vNext LTSC Preview – Build 17623, if you are looking for the Full GUI version.
Use the following keys provided by Microsoft (https://techcommunity.microsoft.com/t5/Windows-Server-Insiders/Announcing-Windows-Server-2019-Preview-Build-17623/m-p/173715#M268)
Windows Server 2019 Build 17623 is available in ISO format in 18 languages. This build and all future pre-release builds will require use of activation keys during setup. The following keys allow for unlimited activations:
|
Datacenter Edition |
6XBNX-4JQGW-QX6QG-74P76-72V67 |
|
Standard Edition |
MFY9F-XBN2F-TYFMP-CCV49-RMYVH |
So, what features to look for in the new in Server 2019:
· Cluster Sets, the new cloud scale-out technology, is a loosely-coupled grouping of multiple Failover Clusters: compute, storage or hyper-converged. Cluster Sets technology will enable virtual machine fluidity across member clusters within a Cluster Set and a unified storage namespace across the “set” in support of virtual machine fluidity.
· Failover Cluster without NTLM authentication, which allows failover clusters to be deployed in environments where NTLM has been disabled.
· Shielded VM’s Offline mode, Alternate HGS and Shielded Linux support, which allows you to run HyperV shielded virtual machines on hosts that suffer intermittent connectivity to their Host Guardian Service (HGS). The fallback HGS will allow you to configure a second set of URLs for Hyper-V to try if it can’t reach the primary HGS server.
· Shielded VM’s Alternate HGS, which allows you to run HyperV shielded virtual machines on hosts that suffer intermittent connectivity to their Host Guardian Service (HGS). The fallback HGS will allow you to configure a second set of URLs for Hyper-V to try if it can’t reach the primary HGS server.
· Shielded VM’s Offline mode, which takes the high availability promise for shielded VMs one step further and allows you to continue to start up a shielded VM even if the host’s primary and fallback HGSs can’t be reached.
· Shielded VM’s Shielded Linux support, for customers that run mixed-OS environments, Microsoft now supports Ubuntu, Red Hat Enterprise Linux, and SUSE Linux Enterprise Server Shielded virtual machines.
· Encrypted Network in SDN, which provides simple to configure DTLS-based encryption using the Network Controller to manage the end-to-end encryption and protect data as it travels through the wires and network devices between the hosts., enabling the VM to VM traffic within the VM subnet to be automatically encrypted as it leaves the host and prevents snooping and manipulation of traffic on the wire. This is done without requiring any configuration changes in the VMs themselves.
· Performance history for Storage Spaces Direct, which allow Administrators of Storage Spaces Direct get easy access to historical performance and capacity data from their cluster.
· Windows Defender Advanced Threat Protection, ,which provides deep platform sensors and response actions, providing visibility to memory and kernel level attacker activities and abilities to take actions on compromised machines in response to incidents such as remote collection of additional forensic data, remediating malicious files, terminating malicious processes etc.
· Windows Defender ATP Exploit Guard ,which is new set of host intrusion prevention capabilities, designed to lock down the device against a wide variety of attack vectors and block behaviours commonly used in malware attacks:
To DOWNLOAD, Join the program to ensure you have access to the bits.
For more details on this preview build, check out the Release Notes.