Archive
Last days to register for ExpertsLive Australia
Connect with like-minded professionals, peers, and potential mentors or collaborators. Networking can open doors to new career opportunities and foster meaningful relationships within the tech community. Register at https://www.expertslive.au

We are closing the registrations very soon. Last Days!
Looking for another reason to attend? Join me on an insightful session to explore how to deploy a Secure and Compliant Azure Cloud environment.
Register now and join us at ExpertsLive Australia 2023 for an unforgettable experience!
Experts Live Australia – Call for Papers is open
Experts Live Australia brings to you two days (September 19th- 20th, 2023) full of engaging sessions with a 100% focus on Microsoft solutions in the areas of cloud, security, data, Open AI and modern workplace technologies.
Experts Live Australia is a community-driven IT conference focused on Microsoft cloud, Security, Data, AI and Modern Workplace Technologies.
Session Information:
- We are looking for a great mix of sessions focused on Microsoft tech topics, including all products within Microsoft 365 and Azure
- Sessions start from level 100 (foundational) and go technically deep to level 400 (expert)
- A session takes 45 minutes for content, demos and Q&A.
- We encourage you to submit multiple sessions!
- We are looking for Microsoft MVPs, RDs, Microsoft employees, and anyone in the community who loves to speak at conferences and share their knowledge and passion for Microsoft technologies.

Which industries are most under threat, and what is the most frequently used cyberattack methods?
Examining the development of spam and advanced threats: 40% of all incoming emails pose a potential threat
Cybercrime remains one of the biggest threats worldwide, according to a new report from email cloud security and backup provider Hornetsecurity. The Cyber Threat Report Edition 2021/2022 details the latest insights and data on the current threat situation with a focus on email communication. The report examines the development of spam and advanced threats, shows which industries are most under threat, and identifies the most frequently used cyberattack methods. It also reviews the most crucial cybercrime-related events of the past year.
As the primary means of communication for business, email is one of the main gateways for cybercrime and remains a prime attack vector. Threat researchers at the Hornetsecurity Security Lab found that 40% of all inbound emails out of the total email traffic during the research period posed a potential threat. This includes spam, phishing emails, and advanced threats such as CEO fraud and any type of malware.
Phishing, malicious links, and ransomware are among the most popular attack tactics used by hackers. “Brand impersonation” is especially popular. For this, cybercriminals copy a company‘s corporate design and mimic the sender address in such a way that it can hardly be distinguished from the original, genuine email address. The main aim is to obtain the user’s access data or to spread malware via hidden links. At 16.5%, Deutsche Post and DHL are among the top five most frequently imitated brands.
In addition to this and other insights about the current state of global cybercrime, the Cyber Threat Report Edition 2021/2022 also provides an outlook on further possible developments.
Get your free copy of the Cyber Threat Report today, and access all data, figures, and visuals!
You know you’re a SysAdmin when…
Did you know that 29% of data loss cases are caused by accident? As World Backup Day nears, we think back to all the incidents, data loss scares, and near-disasters that we’ve experienced over the years – and how grateful we were to have backup during those times!

If you use Microsoft 365/Office 365, Hyper-V or VMware, celebrate with Altaro. All you have to do is sign up for a 30-day free trial of either Altaro VM Backup or Altaro Office 365 Backup – it’s your choice!
What can you win?
• Receive a guaranteed $20 Amazon voucher when you sign up for and use the trial of Altaro Office 365 Backup or Altaro VM Backup
– Get a chance to WIN one of our Grand Prizes when you complete the sentence “You know you’re a SysAdmin when…” What are you waiting for? Sign up now!
How Azure Stack HCI is forcing changes in your datacenter – free webinar
This Altaro FREE webinar, will talk about the key developments and how they will impact the datacenter management. Microsoft MVP Andy Syrewicze will be joined by fellow MVP and Azure Stack HCI expert Carsten Rachfahl to break down and demo live Azure Stack HCI.

Andy and Carsten will help in preparation for these major developments and if attendees have any questions about hybrid cloud or Azure Stack HCI, they can get them answered by these experts during the webinar Q&A.
Learn more and register: How Azure Stack HCI is forcing changes in your datacenter
Don’t miss out on this comprehensive lesson on how to navigate and integrate Azure Stack HCI into your datacenter management.
Save your seat for March 23rd!
How to Get the Most Out of Windows Admin Center – Free eBook
If you have experience with the Windows Admin Center, you might already have deduced it is a powerhouse of functionality making light of important server management tasks. If you’re just adding it to your system administrator toolbox, welcome to the wonder of Windows Admin Center!
With so much functionality, figuring out where to focus is key. Whether you’re just setting out with Windows Admin Center or wanting to realize its full potential, start with Altaro’s free 160+ page second edition eBook, How To Get The Most Of The Windows Admin Center.
Written by Microsoft Cloud & Datacenter Management MVP Eric Siron, it covers the latest developments like the Control Azure Stack HCI, use of WinRM over HTTPs and integration with Azure Monitor, amongst others. It’s a comprehensive guide on everything from installation methods and security considerations to integrating Windows Admin Center into an existing environment. There is even a brief history lesson along with a comparison to alternatives so you should get a solid overview of Windows Admin Center, why chose it and how to work with it.
An all-new server management experience when it was introduced, Windows Admin Center modernized administrative activities with a centralized HTML 5 web application. Just add servers, clusters, desktops, and Azure virtual machines into a personalized, persistent interface, and manage their roles, features, software, registry, PKI certificates, and more. And with Microsoft’s latest investment into the Windows Admin Center and new functionality, there is now even more server management power to work with.
Learn to simplify and optimize your server management tasks – Download your free eBook now!
Ready for another SysAdmin Horror Stories ?

The previously published SysAdmin Horror Stories Vol.1 and Vol.2 highlighted some of SysAdmins’ funniest and most horrifying stories. They proved so successful, that Altaro decided to produce a third and final edition: they’ve gathered some more real-life stories to share with you, that are both funny and horrific!
We all know that a SysAdmin’s job is no easy task, and apart from constantly having systems to update, bugs to fix and users to please, SysAdmins encounter all sorts of situations throughout their careers.
From tech situations to funny anecdotes, terrible mishaps or incidents with colleagues, this eBook includes real stories of what SysAdmins go through on a daily basis. It’s very easy to download as no registration is required.
Click on Download and it’s yours. It includes more than 20 short stories. I hope you’ll enjoy them as much as I did!
What’s New in Windows Server 2022
Get the full lowdown on Windows Server 2022 and its implications for IT admins from expert Microsoft MVPs Andy Syrewicze and Paul Schnackenburg in this unmissable upcoming webinar from Altaro/Hornetsecurity on 13 October. They will explain the full new feature set, security enhancements, editions and license comparisons, where Hyper-V Server has gone, where Azure Stack HCI fits into this discussion, and more!
So, what does this mean for the future of system admins? How will your daily operations change due to the cloud-hosted strategy shift?
The presenters will also be answering all your burning Windows Server 2022 questions so come prepared and make the most out of this event to prepare your organization for the next generation of IT workloads!
Azure Resource Visualiser: Visualising Resources in the Azure Portal
I have been working on a series on Architecture Templates for Azure to streamline the Cloud adoption and migration of workloads to Azure. Those templates that I called Resource Zones are pre-defined architecture that considers the workloads and the Azure Services that are enabled for particular customer.

Each Resource Zone essentially represents the common elements, such as app, db, storage, which shares network connectivity, monitoring and IAM across instances of these archetypes and must be in place to ensure that applications have access to the shared components when deployed.
Coincidence or nor, recently, I noted the Azure Resource Visualiser in the Azure Portal. How cool is the new feature! It lets you visualise the Resources deployed on a Resource Group. It is great to visualise the Resources in a Azure Resource Group and identifying their dependencies. You can select which resources to show and save the image.

If you’re a Microsoft 365 administrator…
Backed by Hornetsecurity’s, 365 Threat Monitor is a free mobile app that detects any threats that breach your Office 365 security and enter your system, enabling you to instantly delete them with just one click: Prevent any damage and save the day!
How it works
Use 365 Threat Monitor for free to receive real-time alerts about gaps in your Office 365 security, and delete ransomware, spam and business email compromise attempts. This free email security mobile app gives you real-time alerts when malware infiltrates your system and allows you to delete it remotely, wherever you are.
- Real-time malware detection and alerting
- Protection you can count on
- Instant deletion of malicious emails
- Threat statistics and reporting
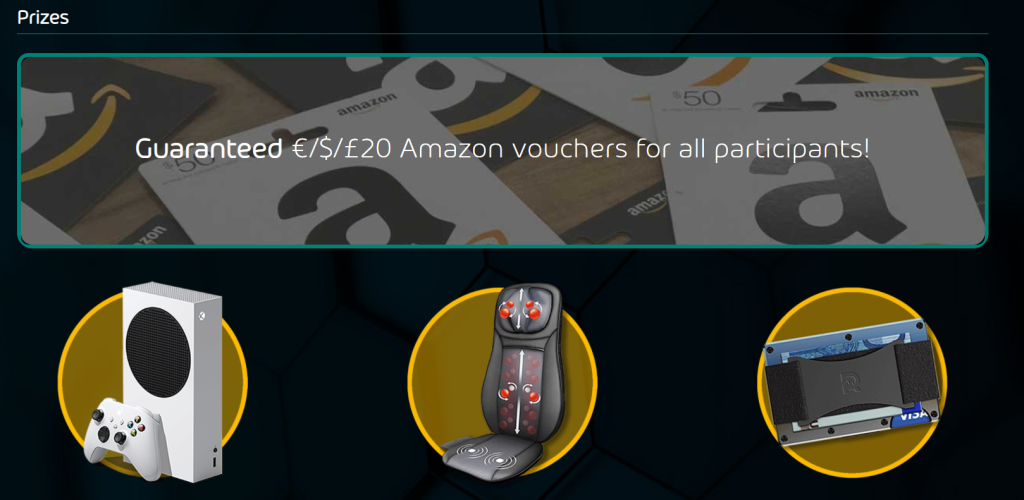
For SysAdmin Day there an interesting contest that might interest you
HornetSecurity is giving away a €20 Amazon voucher if you signup for a for a 30-day free sign up for free to 365 Threat Monitor and set up an account!
Plus you have a chance to win one of their other grand Prizes.
What are you waiting for? Get your free 365 Threat Monitor App & Win!
Note:
Contest entries will be accepted until 15 September, 2021. Only valid Microsoft 365 administrator email addresses will be considered as an eligible entry. Only one entry per individual is permitted. Read full T&Cs.
For any questions related to the SysAdmin Day Contest 2021, please email win@hornetsecurity.com.