Archive
Security: Impunity leads to cyber crime to operate widely free in Brazil
There are evidences that Brazilian cyber criminals are cooperating with the Eastern European gangs involved with ZeuS, SpyEye and other banking Trojans, sharing know-how and exchanging favours.
With almost no legislation and very few arrests, the Brazilian cyber-criminals are motivated on ripping off their own fellow nationals and local businesses.
Sadly, the Brazilians are bracing for another tough year. With a high level of corruption in all levels of the government, no investments in education and with an legislation from the stone age, the cyber criminals have the certain of no punishment and are making many victims.
See 6 tips for staying safer online
A global survey conducted by ESET revealed that between January and November 2015, Brazil had the highest levels of global spread of some of the major banking Trojans, corresponding for 82% of all global detections of the TrojanDowloader.Banload, 72% of the Spy.Bancos and 52% of the Spy.Banker.
In 2014 Brazil was ranked the most dangerous country for financial cyber-attacks. As shocking as it sounds, sensitive data about almost every Brazilian citizen in the open.
As a safe measure, make sure you check the source of the document before you click and download it to your device – The Win32 / TrojanDownloader.Banload is a family of malware that focuses on breaking into the security solutions and perform download other malicious code aimed at stealing bank details.
To minimize the risks, at the personal level, make sure you use strong passwords, don’t share personal information on social network and use multi-authentication factor allied with an updated anti-virus and host firewall.
Many of these malicious codes are based on social engineering and pose as a trusted document in order to deceive their victims – This particular threat (Win32 / TrojanDownloader.Banload) pretends to be an Office document, however, has a double extension .docx_.scr. Its propagation occurs, especially through e-mails, where users believe that this is a Word document, when it is actually an executable file.
No matter your size or the size of your organisation. No one is too small to be a target for cyber criminals.
Do you think that you are safe here in Australia or anywhere in the world? The cyber criminals have no borders. According to the ESET Virus Radar, the number 1 threat is the Win32/Bayrob, followed by the JS/Exploit.Agent.NKZ.
My personal note to you: Start 2016 by making sure your systems are up to date, that you have an anti-virus and host firewall installed and updated and that you follow the basics of security. Visit the Microsoft Safety and Security Center at https://www.microsoft.com/security/default.aspx
If you interested in learn more about the cyber crime, there is an interesting white paper published by Trend Micro, which I recommend.
Sources:
- http://www.welivesecurity.com/2015/05/07/cpl-malware-brazil-white-paper-now-available/
- https://securelist.com/files/2015/11/KLReport_CyberUnderground_Brazil_eng.pdf
- https://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp-ascending-the-ranks.pdf
- http://www.virusradar.com/?utm_source=virus_radar&utm_medium=infohub&utm_campaign=virus_radar
Image: Freedigitalphotos/Stuart Miles
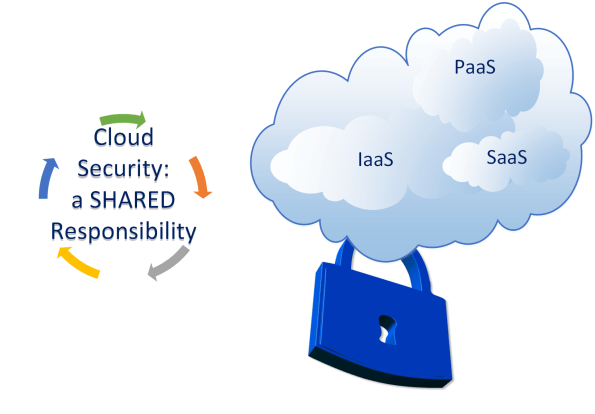
Is Security a cloud benefit or a shared responsibility?
Cloud adoption is skyrocketing and there is no doubt about it, with more and more customers realising its benefits: costs, flexibility, availability, etc.
But how about security? Is security a cloud benefit? Well, sort of. By migrating your systems to a public cloud you certainly be assured that the providers are substantially invest on security measures, policies and certifications to guarantee the underlying infrastructure is a safe place for you to store your data and run your applications. But it stops there.
The conversation you should be having with your cloud provider is not if they are secure. They are! They have all the industry standards and certifications to guarantee that. What you should be asking is if they have real-time data, metric and resources to enable and help you to protect your company data.
The security boundaries are limited to the infrastructure of the public cloud. It is your business responsibility to make sure that your application runs safely and your data is protected and some business don’t get it.
Last week when attending a session at the MVP Summit with Brad Anderson about Identity and cloud, I realised how fragile is the conversation that is happening between organisations and the cloud providers – customers are adopting cloud with security in their mind set (In a recent study of IT decision makers by BT, more than three quarters of the respondents (76%) said that security is their main concern when it comes to cloud-based services and). But many of those customers are putting the responsibility to protect their data, solely on the public cloud provider and that is mistake that needs to be addressed.
Let’s take the example of a customer that migrated their email and documents to the cloud: among others benefits, data availability (anywhere, anytime, any device) is in my opinion one of the great cloud realisations. But the data availability also brings a security risk to organisations if they don’t invest on securing and protecting their data from non-authorised access.
Employees who access privileged company data from public Wi-Fi for example are susceptible to all sorts hackers and they have a high risk of having their device compromised. Have you thought about that? Does your company have VPN or other security measures for external access to the company data?
Also, a password only to protect someone from logon on your computer is not sufficient to protect any data you have on it. Is your company making use of solutions to encrypt the local disk? Does your company have policies in place to prevents that company data is not stored locally on your computer?
And how about your mobile? Ransomware is on the rise, with hackers taken over an entire system, holding it hostage until a fee is paid. Take the Whatsapp example – in August 2015, hackers discovered a bug that enabled them to infect devices for those utilising the web version of the app. On another example, you may recall that Lenovo faced trouble earlier this year, when it found that some of its mobiles and notebooks were sold with pre-installed spyware (According to G DATA researchers it happened somewhere along the supply chain by an outside party). The same problem happened with Huawei, Xiaomi and others.
By not having security measures on your mobile, you could let a thief to access your personal and company data if it gets stolen or lost –
- Do you have a pin to protect your mobile?
- Is your PIN strong enough or something like 1234 or 0000 or your birthday?
- If you search yourself on the internet can any of the information led to your password or PIN?
- Is your company using a device management solution?
A couple of months ago, when running a workshop to architect a solution for a customer to migrate their email to the cloud, I heard incredible the request of their IT manager: “whereas cloud concerns, the solution we want should encompass that some groups of employees should only have access to company email if they are physically connected to our network and data access should be protected from unauthorized people and devices.”.
First you will think that in the cloud times, requests to not allow the data from being accessed outside the company network would not make sense and it is a weird request, as one of the benefits of having the email in the cloud is actually being able to access it elsewhere from any device, right? But the reason is simple: they realised that migrating their email to the cloud, did not mean that their security measures and policies to protect their most precious asset: their customer’s data should not be in place. Their request was true and valid and it got me by surprise as a very few customers really understands that security in the cloud is a shared responsibility.
Security is one on the key concerns when a business decides to migrate to a public cloud and although most of them understand that the level of risk mostly relates to the behaviour and culture of their employees, some still don’t have strict policies in place and lack data access controls, which poses a high risk on their main asset: their data.
I have large experience in Security, Cloud and Datacenter Management. Reach me out and we can organize a workshop for your business at ac@cloudtidings.com
More info on the main public cloud providers security compliance:
- Microsoft For Azure : https://azure.microsoft.com/en-us/support/trust-center/
- Amazon AWS: https://aws.amazon.com/compliance/pci-data-privacy-protection-hipaa-soc-fedramp-faqs/
- VMware VCloud Air: http://vcloud.vmware.com/au/service-offering/security-overview
Cloud and Identity Access
Identity and Access
Controlling who can access which resources is key for Cloud projects. Recently I was talking with a customer that has external users (partners) and internal users and the ability to centralize and manage the access for those users is essential.
Azure provides ways for customers to federate user identities to Azure Active Directory as well as enabling Multi-Factor Authentication and the new Role Based Access Control (RBAC) features can be used to restrict access and permissions for specific cloud resources.
Monitoring
To help detect suspicious access, Azure Active Directory offers reports that alert you to anomalous activity, such as a user logging in from an unknown device. In addition, operational logging and alerting capabilities can notify customers if someone stops a website or if a virtual machine is deleted. It is possible also to use an on premise System Center Operations Manager to monitor the availability and performance of resources that are running on Windows Azure.
The reports provides up to 30 days of data representing key changes in the directory, providing the action, timestamp, the user/application that performed the action, and the user/application on which the action was performed.
Network
With new VNET-to-VNET connectivity, multiple virtual networks can be directly and securely linked to one another. In addition, ExpressRoute is now generally available, enabling customers to establish a private connection to Azure datacenters, keeping their traffic off the Internet. Building on those enhancements, Microsoft also introduced Network Security Groups for easier subnet isolation in multi-tier topologies.
Security
Azure uses industry-leading capabilities, including recent enhancements to TLS/SSL cipher suites and Perfect Forward Secrecy, to encrypt content flowing over the internet between the customer and the Azure service
Microsoft is committed to advancing cloud security with a goal to not only meet, but exceed the level of protection most enterprises have in place on-premises or in their own datacenters. For the latest information on security features and best practices, visit the Microsoft Azure Trust Center.
Azure: Security
Microsoft published an infographic about security in Azure. The Infographic is an overview of security, privacy, and compliance in Azure and it is a great place to start if you are unsure about security in the Cloud space.
You can download the infographic here : http://azure.microsoft.com/en-us/documentation/infographics/cloud-security/
You can find more about Security in Azure here:
- Security, Privacy, and Compliance Whitepaper. New whitepaper details how Azure helps customers achieve the economic benefits of the cloud while furthering security and compliance.
- Privacy Overview Whitepaper.New whitepaper describes how Azure helps safeguard the privacy of customer data in the cloud.
- And much more on the newAzure Trust Center Resourcespage.
Windows Server 2008 R2 Security Baseline : Solution Accelerators
| Elevate the security of Windows Server 2008 R2.
The Windows Server 2008 R2 Security Baseline, in combination with the Security Compliance Manager tool, is designed to help your organization plan, deploy, and monitor the security of Windows Server 2008 R2. This release also includes a Windows Server 2008 R2 settings pack, enabling you to define baselines that include settings outside the scope of the security baselines from Microsoft. To get the public release of this security baseline, download the Security Compliance Manager. |
New security baselines for SQL Server
New security baselines for SQL Server 2008 and SQL Server 2008 R2 now available for beta download.
The latest security baselines in this beta review program are designed to help you plan, deploy, and monitor the security of Microsoft SQL Server 2008 and SQL Server 2008 R2.
The baselines are formatted for import using the Security Compliance Manager, which provides guidance and tools to help you balance your organization’s needs for security and functionality.